{{currentView.title}}
March 25, 2016
Iranian cyberattacks: What the Justice Department's indictment means and what it doesn't
The Justice Department’s indictment of seven Iranian hackers for a “coordinated cyber assault” against 46 major financial institutions and a New York dam on March 24 was a good symbolic gesture, even though there is no measurable chance that any real action against the Iranian attackers will result. Many of the details in the indictment are not particularly surprising, however. The Islamic Republic has conducted an extensive, aggressive, and well-documented cyber campaign targeting U.S. and other foreign entities for years and is likely to expand its efforts further with the influx of cash and technology resulting from the nuclear deal.
Let us first turn to the indictment itself. During a period between 2011 and 2013, the hackers allegedly scanned the Internet for vulnerable computers, exploited them, and used them to attack the servers of U.S. financial institutions. They also leased servers in the U.S. to coordinate these attacks. One of the hackers was also charged with attempting to gain access to the Supervisory Control and Data Acquisition (SCADA) systems of a dam near New York City. SCADA systems run critical infrastructure. It appears from the indictment that only happenstance prevented the hackers from being able to control the dam’s sluice gates. This incident should be a wake-up call. It underscores the vulnerability of our critical infrastructure to hacking as well as to the intent of Iranian elements to exploit that vulnerability.
The indictment indicates that the hackers and the companies they worked for have clear ties to the government and, in particular, the Islamic Revolutionary Guards Corps (IRGC). At least two of the indicted hackers also have ties to the Ashiyane group, which is one of Iran’s largest hacking groups and has publically claimed to perform hacking activities on behalf of the regime. Ashiyane’s leader, Behrooz Kamalian, is the subject of EU sanctions for his role in publicly identifying protestors during the 2009 unrest in Tehran, some of whom were subsequently arrested. The cyber-attacks against the U.S. financial system in 2011-2013 have been assessed as likely a retaliation for U.S. financial sanctions against the nuclear program.
Iranian cyber activity continued after 2013, however, as the Critical Threats Project and others such as Cylance have documented. The Critical Threats Project found that malicious activity emanating from Iranian IP addresses used to probe Norse Corporation’s Intelligence Network increased significantly between 2014 and 2015, for example. U.S. government officials have been reluctant to assert that the Iranian government itself ordered cyberattacks against the U.S., however. But Tehran is well known for delegating its cyber-operations to proxies, which gives the regime plausible deniability and obscures targets for retaliatory action. CTP’s report also showed that some of the Internet probing observed on Norse systems from 2014 to 2015 originated on systems controlled by the Islamic Revolutionary Guards Corps itself.
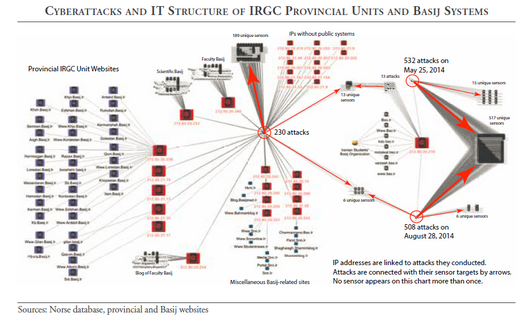 CTP also found that many of the same behaviors mentioned in the indictment could be observed in Iranian hacking patterns in 2014-2015, such as efforts to compromise U.S. systems, the use of IT infrastructure hosted in the West, and the desire to target platforms that would have appeared like a SCADA system to any potential hacker. Iranian cyber activities may be picking up again after a quiet period around the signing of the nuclear deal. U.S. government officials reported a “flurry” of Iranian hacking during the fall of 2015 that targeted the social-media accounts of Obama administration officials, for example.
CTP also found that many of the same behaviors mentioned in the indictment could be observed in Iranian hacking patterns in 2014-2015, such as efforts to compromise U.S. systems, the use of IT infrastructure hosted in the West, and the desire to target platforms that would have appeared like a SCADA system to any potential hacker. Iranian cyber activities may be picking up again after a quiet period around the signing of the nuclear deal. U.S. government officials reported a “flurry” of Iranian hacking during the fall of 2015 that targeted the social-media accounts of Obama administration officials, for example.
Iran is well poised to escalate its cyber-operations moving forward. Iran’s IT sector will likely experience a boom as capital and new technology flow into the country in the wake of the nuclear deal. The Supreme Leader himself has made the development of Iran’s IT sector a key priority for the regime. Tehran, meanwhile, has become increasingly embroiled in regional tensions that threaten to escalate further in the cyber-realm. The Justice Department has made the correct albeit overdue first-step in sending a message to Tehran that it will not tolerate aggressive behavior in cyberspace. It hopefully will not be the last.
To learn more about CTP's research on Iran's cyber capabilities, read the report, "The growing cyberthreat from Iran."